Audit Policy can help you audit compliance with important business-related and security-related rules by tracking precisely defined activities. If you set an Audit Policy for an account locked out, it will audit security events generated by a failed attempt to log on to the locked account. Success audits record successful attempts and failure audits record unsuccessful attempts.
Microsoft recommends that we use the account lockout feature to help deter malicious users and some types of automated attacks from discovering user passwords. This article will show you how to set an Audit Policy for an account in Windows 8.1/8/7.
To work with Audit Policy, you'll have to set it before the Account Lockout Threshold for Invalid Logon Attempts.
Free Download Free DownloadConfiguring the Account Lockout Audit Policy in Windows 8.1/8/7
Follow steps below to set Audit Policy to trace the "Success" and "Failure" logons, password change attempts and policy changes in the Event Viewer.
- Press the Windows + R keys to open the Run dialog, type secpol.msc, press Enter. If prompted by UAC, click/tap on Yes.
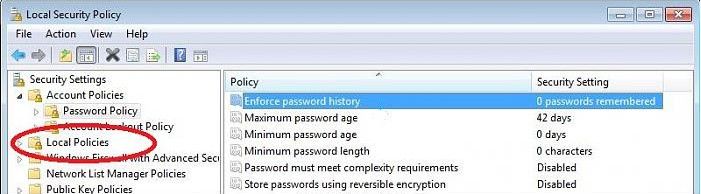
- In the left pane, expand Local Policies, and then click on "Audit Policy". On the right side, search for "Audit account logon events".
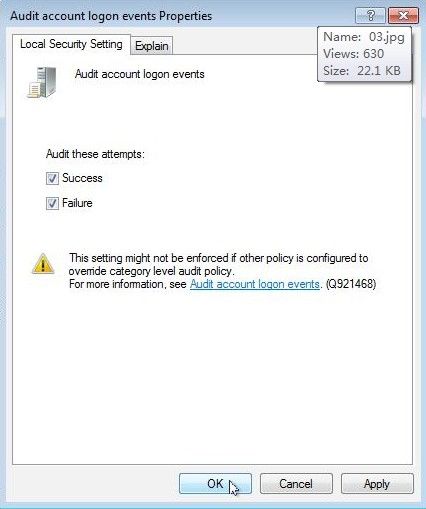
- Right click Properties: Check both box "Success" & "Failure", and click OK when you are done.

- After the Audit Policy is configured, the following event appears on your computer if there is a failed attempt to log on.
Event ID Event message 4625 An account failed to log on.
Now you can go to the "Event Viewer" and see how many attempts had been made to Log On on your computer while you are not in.
World's 1st Windows Password Recovery Software to Reset Windows Administrator & User Password.
Free Download Free Download