In this article we will fully show you how to capture wireless packets with Wireshark, a popular network protocol analyzer. It can capture and/or show the data packets for Ethernet, Wi-Fi, Bluetooth, and other hundreds of other network protocols, depending upon the platform and network adapter you're using. It supports reading/writing from/to many different capture file formats and supports exporting to a few different formats.
Tutorial on How to Sniff Wireless Packets with Wireshark
Follow steps below to capture packets easily and quickly with Wireshark:
Installing Wireshark
Go to http://www.wireshark.org/download.html , download the software for your applicable operating system, and perform the installation.
Capture Packets
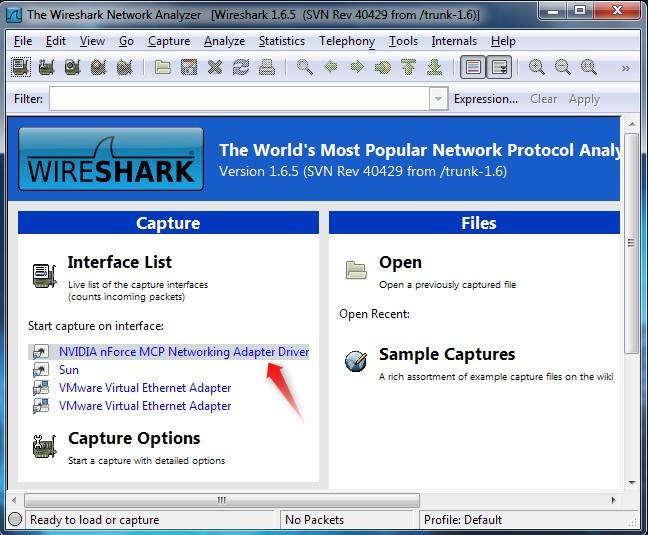
- After downloading and installing Wireshark, you can launch it and click the name of an interface under Interface List to start capturing packets on that interface. To capture traffic on the wireless network, click your wireless interface.
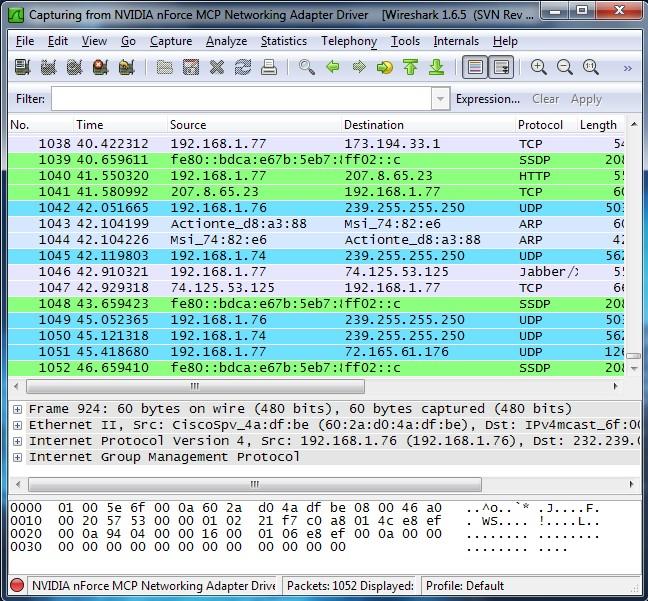
- Once you click the interface's name, you'll see the packets start to appear in real time. Wireshark captures each packet sent to or from your system. If you're capturing on a wireless interface and have promiscuous mode enabled in your capture options, you'll also see other packets on the network.
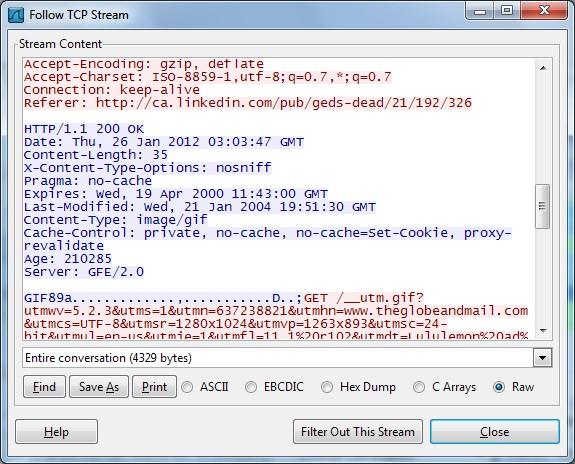
Note: Wireshark uses colors to help you identify the types of traffic at a glance. By default, green is TCP traffic, dark blue is DNS traffic, light blue is UDP traffic, and black identifies TCP packets with problems. - Right click a packet and select Follow TCP Stream. You'll see the full conversation between the client and the server.
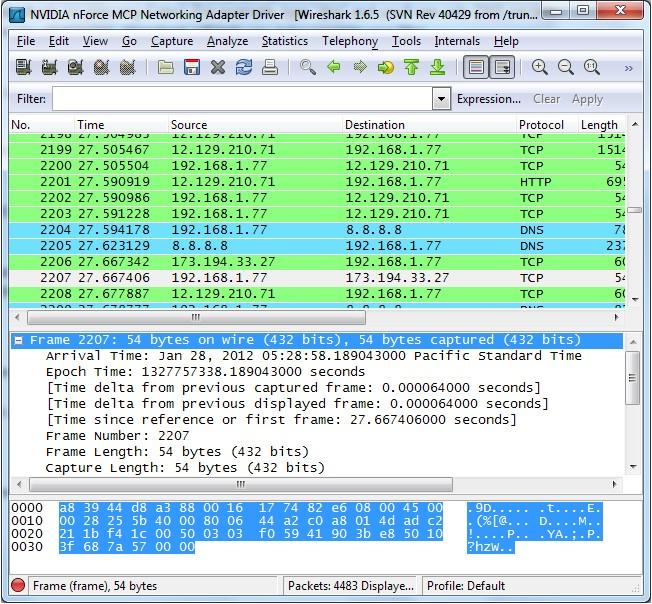
- Click a packet to select it and you can dig down to view its details.
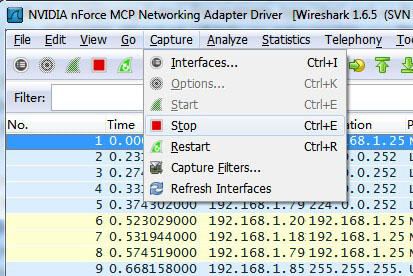
- Packet captures can result in fairly large files if left running for long. You only need to capture about 10 seconds of traffic. After this time click Stop by clicking Capture on the top menu and then Stop.
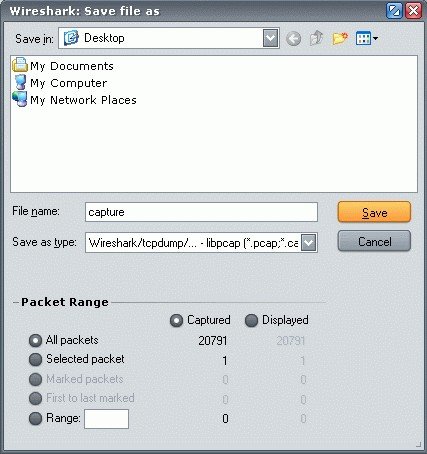
- You can save captured packets simply by using the File → Save As… menu item. You can choose which packets to save and which file format to be used.
Note: Wireshark uses the libpcap file (.cap, .pcap) format as the default format to save captured packets. This file can be imported to Wi-Fi Password Recovery for further password recovery.
Now you have a clear idea about how to capture wireless packets and get the WPA capture files to import the captured packets to attack the network password. For details about how to use Wireshark, you can go to the official tutorial (https://www.wireshark.org/docs/wsug_html_chunked/ChapterIntroduction.html).